hmmm
Category: Privacy,
Google Urged the U.S. to Limit Protection For Activist Workers
While Google publicly supported employees who protested company policies, it quietly asked the government to narrow the right to organize over work email.
…Google, whose employees have captured international attention in recent months through high-profile protests of workplace policies, has been quietly urging the U.S. government to narrow legal protection for workers organizing online
…Google has long fostered a culture of employee feedback, allowing open debate in meetings and online forums, where staff have advocated for changes to products and facilities over the company’s 20-year history. But the last year has seen an unprecedented wave of concentrated and forceful advocacy from employees, often at direct odds with the positions of management. After Google was awarded a Pentagon contract for using artificial intelligence to analyze drone footage, thousands of employees signed a petition demanding Google remove itself from “the business of war,” nine software engineers refused to work on a security feature that could help the company win more military contracts, and in June the company said it wouldn’t renew its Department of Defense deal. An employee introduced a shareholder resolution to tie executive compensation to diversity and inclusion, while others wrote a letter to their chief executive officer decrying the treatment of sub-contracted staff as “part of a system of institutional racism, sexism, and discrimination.”
…Google’s objections to the legal protection for employees organizing via employee email came in filings defending itself against allegations brought by a regional director of the NLRB. In a 2017 complaint, the agency had accused Google of violating federal labor law, including by maintaining workplace policies that infringe on workers’ rights and by making threats against employees. The complaint also alleged that Google violated the law in 2015 by issuing a warning to an employee because of comments made via email and on the company forum G+ “regarding workplace diversity and social justice initiatives, workplace policy viewpoints, and regarding employees’ rights to express their opinion on G+.”
…The protection established in Purple Communications is “pretty fundamental” given the centrality of email to modern workplace communications, said Wilma Liebman, who chaired the NLRB during Obama’s first term. Given Google’s rhetoric about “the free exchange of ideas, and itself as a purveyor of mechanisms for communications,” she said, “That’s an irony that Google, of all companies, would take such a narrow position.”
Google Urged the U.S. to Limit Protection For Activist Workers – Bloomberg
hmmm
TSA defends ‘Quiet Skies’ monitoring program
The Boston Globe first reported on Sunday that the TSA implemented the “Quiet Skies” program years ago to help eliminate threats posed by “unknown or partially known terrorists.”
Through the program, undercover federal air marshals observe passengers’ behavior. This can include watching how close they stand to the boarding area, how often they use the bathroom and any behavioral tics such as sweating or twitching.
The report included critical accounts of the program from some air marshals, who said they felt it was a poor use of resources to track nonthreatening travelers.
TSA defends ‘Quiet Skies’ monitoring program | TheHill
The TSA sounds more inefficiently and irrationally focused Big Brother than usual in this article. with their record of ineptitude, shouldn’t they be focusing more on the basics and leaving the spy stuff to people who are more qualified, or at least less inept?
Manafort held secret talks with Assange in Ecuadorian embassy, sources say
Manafort’s first visit to the embassy took place a year after Assange sought asylum inside, two sources said.
…Visitors normally register with embassy security guards and show their passports. Sources in Ecuador, however, say Manafort was not logged.
…According to sources, Manafort’s acquaintance with Assange goes back at least five years, to late 2012 or 2013, when the American was working in Ukraine and advising its Moscow-friendly president, Viktor Yanukovych.
Why Manafort might have sought out Assange in 2013 is unclear. During this period the veteran consultant was involved in black operations against Yanukovych’s chief political rival, Yulia Tymoshenko, whom Yanukovych had jailed. Manafort ran an extensive lobbying operation featuring European former politicians.
…One person familiar with WikiLeaks said Assange was motivated to damage the Democrats campaign because he believed a future Trump administration would be less likely to seek his extradition on possible charges of espionage. This fate had hung over Assange since 2010, when he released confidential US state department cables. It contributed to his decision to take refuge in the embassy.
…Last week a court filing released in error suggested that the US justice department had secretly charged Assange with a criminal offence. Written by the assistant US attorney, Kellen Dwyer, the document did not say what Assange had been charged with or when the alleged offence took place.
Manafort held secret talks with Assange in Ecuadorian embassy, sources say | US news | The Guardian
hmmmm
So many people have had their DNA sequenced that they’ve put other people’s privacy in jeopardy
A new study argues that more than half of Americans could be identified by name if all you had to start with was a sample of their DNA and a few basic facts, such as the region where they live and about how old they might be.
More than 1 million Americans have already published their genetic information, and dozens more do so every day.
…One of them is the rise of direct-to-consumer genetic testing. Companies such as Ancestry.com and 23andMe can sequence anyone’s DNA for about $100.
…The other essential element is the proliferation of publicly searchable genealogy databases like GEDmatch. Anyone can upload a full genome to these sites and powerful computers will crunch through it, looking for stretches of matching DNA sequences that can be used to build out a family tree.
…After a long day of painstaking work, they researchers were able to correctly name the owner of the DNA sample.
The authors said the same process would work for about 60% of Americans of European descent, who are the people most likely to use genealogical websites, Erlich said. Though the odds of success would be lower for people from other backgrounds, it would still be expected to work for more than half of all Americans, they said.
…If you can find a person’s third cousin in a genealogical database, then you should be able to identify the person with a reasonable amount of sleuthing, Erlich said.
hmmmmm
Facebook’s Massive Security Breach: Everything We Know
This is the second security vulnerability that Facebook has disclosed in recent months. In June, the company announced it had discovered a bug that made up to 14 million people’s posts publicly viewable to anyone for days. This is the first time in Facebook’s history, though, that users’ entire accounts may have been compromised by outside hackers.
Facebook’s Massive Security Breach: Everything We Know | WIRED
The “geniuses” at facebook sure come off as incompetent and out of their depth, don’t they?
Top Voting Machine Vendor Admits It Installed Remote-Access Software on Systems Sold to States
The nation’s top voting machine maker has admitted in a letter to a federal lawmaker that the company installed remote-access software on election-management systems it sold over a period of six years, raising questions about the security of those systems and the integrity of elections that were conducted with them.
The statement [indicates that previous comments they offered on this subject were outright lies. For example] in February …a spokesperson said ES&S had never installed pcAnywhere on any election system it sold. “None of the employees, … including long-tenured employees, has any knowledge that our voting systems have ever been sold with remote-access software,” the spokesperson said.
…ES&S is the top voting machine maker in the country, a position it held in the years 2000-2006 when it was installing pcAnywhere on its systems. The company’s machines were used statewide in a number of states, and at least 60 percent of ballots cast in the US in 2006 were tabulated on ES&S election-management systems.
…Election-management systems are not the voting terminals that voters use to cast their ballots, but are just as critical: they sit in county election offices and contain software that in some counties is used to program all the voting machines used in the county; the systems also tabulate final results aggregated from voting machines.
Software like pcAnywhere is used by system administrators to access and control systems from a remote location to conduct maintenance or upgrade or alter software. But election-management systems and voting machines are supposed to be air-gapped for security reasons—that is, disconnected from the internet and from any other systems that are connected to the internet.
…The presence of such software makes a system more vulnerable to attack from hackers, especially if the remote-access software itself contains security vulnerabilities. If an attacker can gain remote access to an election-management system through the modem and take control of it using the pcAnywhere software installed on it, he can introduce malicious code that gets passed to voting machines to disrupt an election or alter results.
[Sen. Ron] Wyden told Motherboard that installing remote-access software and modems on election equipment “is the worst decision for security short of leaving ballot boxes on a Moscow street corner.”
…Security researchers discovered a critical vulnerability in pcAnywhere that would allow an attacker to seize control of a system that had the software installed on it, without needing to authenticate themselves to the system with a password. And other researchers with the security firm Rapid7 scanned the internet for any computers that were online and had pcAnywhere installed on them and found nearly 150,000 were configured in a way that would allow direct access to them.
Although Wyden’s office asked ES&S to identify which of its customers were sold systems with pcAnywhere installed, the company did not respond.
“ES&S needs to stop stonewalling and provide a full, honest accounting of equipment that could be vulnerable to remote attacks,” [Wyden]e told Motherboard. “When a corporation that makes half of America’s voting machines refuses to answer the most basic cyber security questions, you have to ask what it is hiding.”
Grrrrrrrrrrrrrrrrrrrrrrrrrrrrrr
How Comey intervened to kill WikiLeaks’ immunity deal
“Subject to adequate and binding protections, including but not limited to an acceptable immunity and safe passage agreement, Mr. Assange welcomes the opportunity to discuss with the U.S. government risk mitigation approaches relating to CIA documents in WikiLeaks’ possession or control, such as the redaction of agency personnel in hostile jurisdictions and foreign espionage risks to WikiLeaks staff,” Waldman wrote Laufman on March 28, 2017.
Not included in the written proffer was an additional offer from Assange: He was willing to discuss technical evidence ruling out certain parties in the controversial leak of Democratic Party emails to WikiLeaks during the 2016 election. The U.S. government believes those emails were hacked by Russia; Assange insists they did not come from Moscow.
“Mr. Assange offered to provide technical evidence and discussion regarding who did not engage in the DNC releases,” Waldman told me. “Finally, he offered his technical expertise to the U.S. government to help address what he perceived as clear flaws in security systems that led to the loss of the U.S. cyber weapons program.”
…Waldman couldn’t believe a U.S. senator and the FBI chief were sending a different signal, so he went back to Laufman, who assured him the negotiations were still on. “What Laufman said to me after he heard I was told to ‘stand down’ by Warner and Comey was, ‘That’s bullshit. You are not standing down and neither am I,’” Waldman recalled.
…Multiple sources tell me the FBI’s counterintelligence team was aware and engaged in the Justice Department’s strategy but could not explain what motivated Comey to send a different message around the negotiations through Warner. A lawyer for Comey did not immediately return calls seeking comment.
…Soon, the rare opportunity to engage Assange in a dialogue over redactions, a more responsible way to release information, and how the infamous DNC hacks occurred was lost — likely forever.
How Comey intervened to kill WikiLeaks’ immunity deal | TheHill
More Comey interference in things related to the outcome of the 2016 election. Huh.
Facebook accused of conducting mass surveillance through its apps
Facebook used its apps to gather information about users and their friends, including some who had not signed up to the social network, reading their text messages, tracking their locations and accessing photos on their phones, a court case in California alleges.
The claims of what would amount to mass surveillance are part of a lawsuit brought against the company by the former startup Six4Three, listed in legal documents filed at the superior court in San Mateo as part of a court case that has been ongoing for more than two years.
…Documents filed in the court last week draw upon extensive confidential emails and messages between Facebook senior executives, which are currently sealed.
…The allegations about surveillance appear in a January filing, the fifth amended complaint made by Six4Three. It alleges that Facebook used a range of methods, some adapted to the different phones that users carried, to collect information it could use for commercial purposes.
“Facebook continued to explore and implement ways to track users’ location, to track and read their texts, to access and record their microphones on their phones, to track and monitor their usage of competitive apps on their phones, and to track and monitor their calls,” one court document says.
…It claims the social media company lured developers and investors on to the platform by intentionally misleading them about data controls and privacy settings. As part of the January filing, it claims Facebook tracked users extensively, sometimes without consent.
On Android phones, the company was able to collect metadata and content from text messages, the lawsuit alleges. On iPhones it could access most photos, including those that had not been uploaded to Facebook, Six4Three claims.
Other alleged projects included one to remotely activate Bluetooth, allowing the company to pinpoint a user’s location without them explicitly agreeing to it. Another involved the development of privacy settings with an early end date that was not flagged to users, letting them expire without notice, the court documents claim.
…It also collected information sent by non-subscribers to friends or contacts who had Facebook apps installed on their phones, the court documents claim. Because these people would not have been Facebook users, it would have been impossible for them to have consented to Facebook’s collection of their data.
…Facebook has not fully disclosed the manner in which it pre-processes photos on the iOS camera roll, meaning if a user has any Facebook app installed on their iPhone, then Facebook accesses and analyses the photos the user takes and/or stores on the iPhone, the complainant alleges.
Facebook accused of conducting mass surveillance through its apps | Technology | The Guardian
hmmmm
Leaked: Cambridge Analytica’s blueprint for Trump victory
[The Trump campaign worked with Cambridge Analytica to] micro-target US voters with carefully tailored messages about the Republican nominee across digital channels.
Intensive survey research, data modelling and performance-optimising algorithms were used to target 10,000 different ads to different audiences in the months leading up to the election. The ads were viewed billions of times, according to the presentation.
…None of the techniques described in the document are illegal. However, the scandal over Cambridge Analytica’s acquisition of data from more than 50 million Facebook users is lifting the lid on an industry that has learned how to closely track the online footprint and daily lives of US voters.
…The Republican nominee, who had just secured sufficient delegates to become the party’s candidate, still had “no speakable data infrastructure” and “no unifying data, digital and tech strategy”, the document states.
…“There was no database of record. There were many disparate data sources that were not connected, matched or hygiened,” she said of the process of ordering, sorting and cleaning enormous data sets. “There was no data science programme, so they weren’t undertaking any modelling. There was no digital marketing team.”
…The document contains very little information about how the campaign used Facebook data. One page, however, suggests Cambridge Analytica was able to constantly monitor the effectiveness of its messaging on different types of voters, giving the company and the campaign constant feedback about levels of engagement on platforms such as Twitter, Facebook and Snapchat.
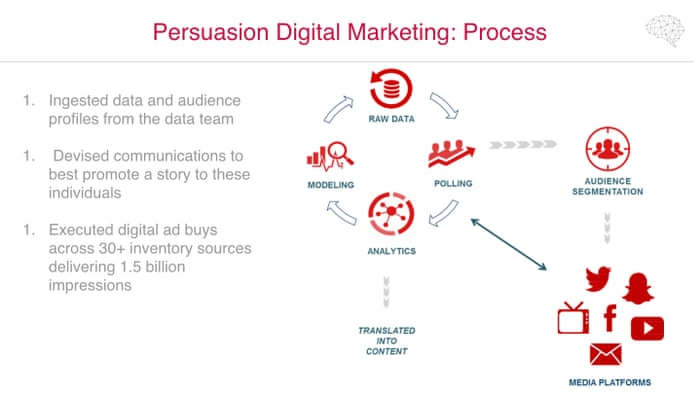
The feedback loop meant the algorithms could be constantly updated and improved to deliver thousands of different messages to voters depending on their profile.
…Voters in areas where people were likely to be Trump supporters were shown a triumphant-looking image of the nominee, and help finding their nearest polling station.
Those whose geographical information suggested they were not fervent Trump supporters, such as swing voters, were shown photos of his high-profile supporters, including his daughter Ivanka Trump, a celebrity from the reality TV show Duck Dynasty, and Dana White, the president of the Ultimate Fighting Championship.
One of the most effective ads, according to Kaiser, was a piece of native advertising on the political news website Politico, which was also profiled in the presentation. The interactive graphic, which looked like a piece of journalism and purported to list “10 inconvenient truths about the Clinton Foundation”, appeared for several weeks to people from a list of key swing states when they visited the site. It was produced by the in-house Politico team that creates sponsored content.
…Advertisements on Facebook, Twitter, Google and the music-sharing app Pandora were used to help convince 35,000 supporters to install an app used by the most active supporters.
According to the presentation, Cambridge Analytica and the Trump campaign also used a new advertising technique offered by Twitter, launched at the start of the election year, which enabled clients to kickstart viral tweets.
The “conversational ads” feature was used to encourage Trump’s followers to tweet using a set of pre-determined hashtags.
The campaign also took advantage of an ad opportunity provided by Snapchat, enabling users to swipe up and immediately see a preloaded web page. While not useful for securing donors, Cambridge Analytica deemed the tool useful for engaging potential voter “contacts”, according to the presentation.
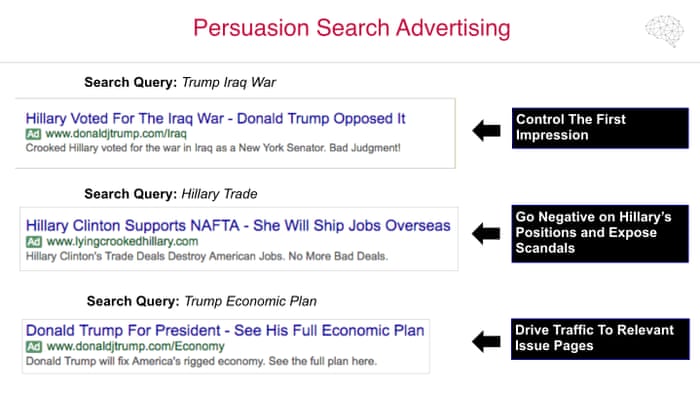
One of the final slides explains how the company used paid-for Google ads to implement “persuasion search advertising”, to push pro-Trump and anti-Clinton search results through the company’s main search facility.
Leaked: Cambridge Analytica’s blueprint for Trump victory | UK news | The Guardian
hmmmm
Facebook Gave 60 Tech Firms Including Apple, Samsung ‘Deep Access’ to User Data-But Denies It Was Wrong
The U.S. social networking website set up data-sharing partnerships with at least 60 phone and tablet makers over the past 10 years. In the exchange, Facebook could expand its reach while the companies could implement features such as “like” buttons and image sharing. It alleged Facebook gave access to user data without consent.
Experts voiced concern that reckless sharing of data could lead to security and privacy risks. Accessed Facebook information, meanwhile, allegedly included political preferences, relationship statuses and upcoming diary dates—even for users who had not given explicit permission for their data to be shared.
The profile information was allegedly obtained via privately-built application programming interfaces (APIs) which are the back-end protocols that are used to develop mobile apps, functions and systems. It has been confirmed that Facebook user data was stored on the technology companies’ servers.
When commodification of your customer base goes wrong and it should have dawned on you that if it wasn’t wrong to treat people, at the very least it was going to come back and bite you on the ass a bit but you never admit any wrong doing or make admissions that might open the corporate entity up to lawsuits so you double-down on delusional and obnoxious positions. Doh!
Seriously, any more of these delusional denials from facebook and I’m going to start rooting for all of the insufferable eggheads who’ve made money of this to be thrown unceremoniously in jail.
Amazon confirms that Echo device secretly shared user’s private audio
Amazon confirms that Echo device secretly shared user’s private audio [Updated] | Ars Technica
[another snicker] Echo listens to and apparently records private audio? No shit, Sherlock?
